
-
Cybersecurity
-
 Document: November 2024 Special Focus: Unmasking the Tool Bloat Problem: Is There Such a Thing as Too Much Security?File: November 2024 Special Focus: Unmasking the Tool Bloat Problem: Is There Such a Thing as Too Much Security?.pdflaunch
Document: November 2024 Special Focus: Unmasking the Tool Bloat Problem: Is There Such a Thing as Too Much Security?File: November 2024 Special Focus: Unmasking the Tool Bloat Problem: Is There Such a Thing as Too Much Security?.pdflaunch -
 Document: September 2024 Special Focus: The Unseen Adversary: Decrypting The Looming Threats of AI Gone Astray IntroductionFile: September 2024 Special Focus: The Unseen Adversary: Decrypting The Looming Threats of AI Gone Astray Introduction.pdflaunch
Document: September 2024 Special Focus: The Unseen Adversary: Decrypting The Looming Threats of AI Gone Astray IntroductionFile: September 2024 Special Focus: The Unseen Adversary: Decrypting The Looming Threats of AI Gone Astray Introduction.pdflaunch -
 Document: N-able: Managed Detection and Response ServiceFile: N-able: Managed Detection and Response Service.pdflaunch
Document: N-able: Managed Detection and Response ServiceFile: N-able: Managed Detection and Response Service.pdflaunch -
 Document: How to balance compliance and personalisation in a privacy-conscious worldFile: How to balance compliance and personalisation in a privacy-conscious world.pdflaunch
Document: How to balance compliance and personalisation in a privacy-conscious worldFile: How to balance compliance and personalisation in a privacy-conscious world.pdflaunch -
 Document: 5 Signs It’s Time to Upgrade Your Identity ProgrammeFile: 5 Signs It’s Time to Upgrade Your Identity Programme.pdflaunch
Document: 5 Signs It’s Time to Upgrade Your Identity ProgrammeFile: 5 Signs It’s Time to Upgrade Your Identity Programme.pdflaunch -
 Document: September 2023 Special Focus: The Rise of Automotive HackingFile: September 2023 Special Focus: The Rise of Automotive Hacking.pdflaunch
Document: September 2023 Special Focus: The Rise of Automotive HackingFile: September 2023 Special Focus: The Rise of Automotive Hacking.pdflaunch -
 Document: July 2023 Special Focus: Cybercrime-as-a-Service: The New Side HustleFile: July 2023 Special Focus: Cybercrime-as-a-Service: The New Side Hustle.pdflaunch
Document: July 2023 Special Focus: Cybercrime-as-a-Service: The New Side HustleFile: July 2023 Special Focus: Cybercrime-as-a-Service: The New Side Hustle.pdflaunch -
 Document: Dell PowerEdge - Cyber Resilient Infrastructure for a Zero Trust world -File: Dell PowerEdge - Cyber Resilient Infrastructure for a Zero Trust world - .pdflaunch
Document: Dell PowerEdge - Cyber Resilient Infrastructure for a Zero Trust world -File: Dell PowerEdge - Cyber Resilient Infrastructure for a Zero Trust world - .pdflaunch -
Document: The State of Cybersecurity Culture Survey ReportFile: The State of Cybersecurity Culture Survey Report.pdflaunch
-
 Document: Sygnia Case Study: Cracking a Global Adversary-in-the-Middle Campaign Using a Threat Intelligence ToolkitFile: Sygnia Case Study: Cracking a Global Adversary-in-the-Middle Campaign Using a Threat Intelligence Toolkit.pdflaunch
Document: Sygnia Case Study: Cracking a Global Adversary-in-the-Middle Campaign Using a Threat Intelligence ToolkitFile: Sygnia Case Study: Cracking a Global Adversary-in-the-Middle Campaign Using a Threat Intelligence Toolkit.pdflaunch -
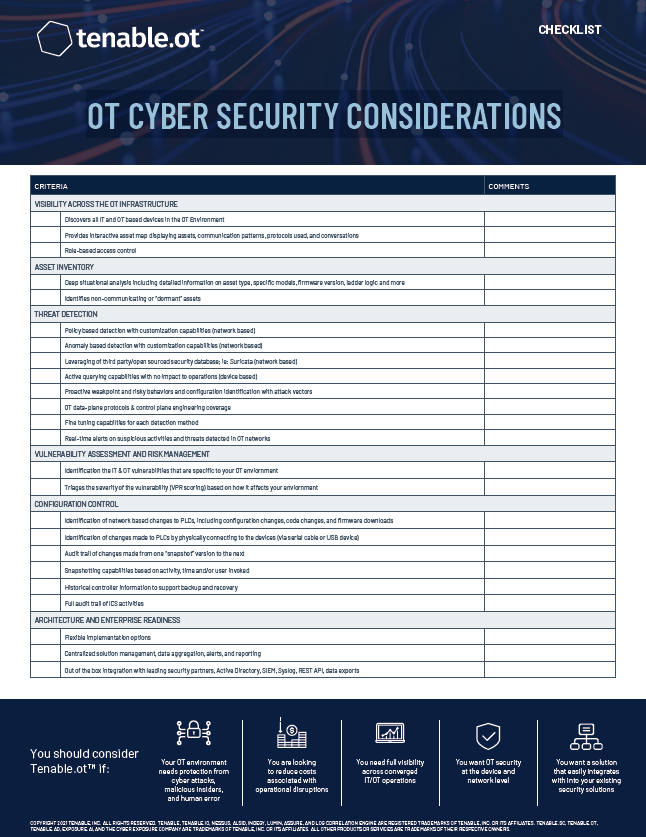 Document: Tenable's OT Cyber Security Considerations ChecklistFile: Tenable's OT Cyber Security Considerations Checklist.pdflaunch
Document: Tenable's OT Cyber Security Considerations ChecklistFile: Tenable's OT Cyber Security Considerations Checklist.pdflaunch -
 Document: Securing Manufacturing: An Active Directory Security PerspectiveFile: Securing Manufacturing: An Active Directory Security Perspective.pdflaunch
Document: Securing Manufacturing: An Active Directory Security PerspectiveFile: Securing Manufacturing: An Active Directory Security Perspective.pdflaunch -
 Document: April 2023 Special Focus: Synthetic Identity Fraud: Dealing With a Digital FrankensteinFile: April 2023 Special Focus: Synthetic Identity Fraud: Dealing With a Digital Frankenstein.pdflaunch
Document: April 2023 Special Focus: Synthetic Identity Fraud: Dealing With a Digital FrankensteinFile: April 2023 Special Focus: Synthetic Identity Fraud: Dealing With a Digital Frankenstein.pdflaunch -
 Document: PowerEdge - Cyber Resilient Infrastructure for a Zero Trust worldFile: PowerEdge - Cyber Resilient Infrastructure for a Zero Trust world.pdflaunch
Document: PowerEdge - Cyber Resilient Infrastructure for a Zero Trust worldFile: PowerEdge - Cyber Resilient Infrastructure for a Zero Trust world.pdflaunch -
 Document: PowerEdge - Cyber Resilient Infrastructure for a Zero Trust world (MY)File: PowerEdge - Cyber Resilient Infrastructure for a Zero Trust world (MY).pdflaunch
Document: PowerEdge - Cyber Resilient Infrastructure for a Zero Trust world (MY)File: PowerEdge - Cyber Resilient Infrastructure for a Zero Trust world (MY).pdflaunch -
 Document: Breaking Through With Modern Security: How CIOs Can Enhance Cyber Resilience (MY)File: Breaking Through With Modern Security: How CIOs Can Enhance Cyber Resilience (MY).pdflaunch
Document: Breaking Through With Modern Security: How CIOs Can Enhance Cyber Resilience (MY)File: Breaking Through With Modern Security: How CIOs Can Enhance Cyber Resilience (MY).pdflaunch -
 Document: ESG Research Summary - Cyber-resiliency Maturity in ServersFile: ESG Research Summary - Cyber-resiliency Maturity in Servers.pdflaunch
Document: ESG Research Summary - Cyber-resiliency Maturity in ServersFile: ESG Research Summary - Cyber-resiliency Maturity in Servers.pdflaunch -
Document: Seamless Application Security: Security at the Speed of DevOpsFile: Seamless Application Security: Security at the Speed of DevOps.pdflaunch
-
Document: CSA's Executive Briefing Note on Simplifying SASE : What Is Secure Access Service Edge and How Can It Help You?File: CSA's Executive Briefing Note on Simplifying SASE : What Is Secure Access Service Edge and How Can It Help You?.pdflaunch
-
Document: 5 Tips for Defending Against RansomwareFile: 5 Tips for Defending Against Ransomware.pdflaunch
-
Document: Cloud Adoption and Risk 2019File: Cloud Adoption and Risk 2019.pdflaunch
-
Document: [E-Book]Securing Your Business With a Security Fabric ApproachFile: [E-Book]Securing Your Business With a Security Fabric Approach.pdflaunch
-
 Document: October 2021 Special Focus: Quantum Safe SecurityFile: October 2021 Special Focus: Quantum Safe Security.pdflaunch
Document: October 2021 Special Focus: Quantum Safe SecurityFile: October 2021 Special Focus: Quantum Safe Security.pdflaunch -
Document: August 2021 Special Focus: Security Process AutomationFile: August 2021 Special Focus: Security Process Automation.pdflaunch
-
 Document: Complexity In Cybersecurity Report 2019File: Complexity In Cybersecurity Report 2019.pdflaunch
Document: Complexity In Cybersecurity Report 2019File: Complexity In Cybersecurity Report 2019.pdflaunch -
Document: May 2021 Special Focus: Securing The invisible PerimeterFile: May 2021 Special Focus: Securing The invisible Perimeter.pdflaunch
-
Document: Thales Data Threat Report APAC Edition 2021File: Thales Data Threat Report APAC Edition 2021.pdflaunch
-
 Document: Build a strong defence against cyberattackFile: Build a strong defence against cyberattacklaunch
Document: Build a strong defence against cyberattackFile: Build a strong defence against cyberattacklaunch -
Document: March 2021 Special Focus: Zero Trust SecurityFile: March 2021 Special Focus: Zero Trust Security.pdflaunch
-
Document: [E-Book] Ensuring Successful Implementation of the Malaysia Cyber Security Strategy (MCSS) 2020-2024File: [E-Book] Ensuring Successful Implementation of the Malaysia Cyber Security Strategy (MCSS) 2020-2024.pdflaunch
-
Document: Infographic: Sharing Corporate Data with Internal and External Users Without Compromising SecurityFile: Infographic: Sharing Corporate Data with Internal and External Users Without Compromising Security.pdflaunch
-
Document: The Key Pillars for Protecting Sensitive Data in Any OrganizationFile: The Key Pillars for Protecting Sensitive Data in Any Organization.pdflaunch
-
Document: Special Focus: Understanding the Need for Zero TrustFile: Special Focus: Understanding the Need for Zero Trust.pdflaunch
-
Document: Thales e-Book: Securing a New Digital LandscapeFile: Thales e-Book: Securing a New Digital Landscape.pdflaunch
-
Document: Upgrading Existing Security Systems to Agile Quantum-Safe with SafeNet Luna HSMs and SafeNet High Speed EncryptorsFile: Upgrading Existing Security Systems to Agile Quantum-Safe with SafeNet Luna HSMs and SafeNet High Speed Encryptors.pdflaunch
-
Document: Taking IT Out Of The Shadows By Shining A Light On Your DataFile: Taking IT Out Of The Shadows By Shining A Light On Your Data.pdflaunch
-
Document: Malwarebytes Infographic: Avoiding the Cybersecurity HubrisFile: Malwarebytes Infographic: Avoiding the Cybersecurity Hubris.pdflaunch
-
Document: Malwarebytes Infographic: Emotet is back! Protect your organisation!File: Malwarebytes Infographic: Emotet is back! Protect your organisation!.pdflaunch
-
Document: How to Choose a Managed Security ProviderFile: How to Choose a Managed Security Provider.pdflaunch
-
Document: Malwarebytes Q2 Report - Cybercrime Tactics and TechniquesFile: Malwarebytes Q2 Report - Cybercrime Tactics and Techniques.pdflaunch
-
Document: How to Choose a Managed Security Provider.File: How to Choose a Managed Security Provider..pdflaunch
-
Document: September 2020 Special Focus: Shadow ITFile: September 2020 Special Focus: Shadow IT.pdflaunch
-
Document: Catching Fraudsters In The Act Anywhere At AnytimeFile: Catching Fraudsters In The Act Anywhere At Anytime.pdflaunch
-
Document: Cybersecurityasean.com Top ASEAN LinkedIn Security Influencers 2020File: Cybersecurityasean.com Top ASEAN LinkedIn Security Influencers 2020.pdflaunch
-
 Document: Blackberry Desktop Enable Secure Remote Connectivity from Any Windows 10 Or MacOS DeviceFile: Blackberry Desktop Enable Secure Remote Connectivity from Any Windows 10 Or MacOS Device.pdflaunch
Document: Blackberry Desktop Enable Secure Remote Connectivity from Any Windows 10 Or MacOS DeviceFile: Blackberry Desktop Enable Secure Remote Connectivity from Any Windows 10 Or MacOS Device.pdflaunch -
 Document: IBM Security Webinar - Best Practices & How Organizations Can Drive a Cybersecurity Behavioural Change Program - REGISTRATION SGFile: IBM Security Webinar - Best Practices & How Organizations Can Drive a Cybersecurity Behavioural Change Program - REGISTRATION SGlaunch
Document: IBM Security Webinar - Best Practices & How Organizations Can Drive a Cybersecurity Behavioural Change Program - REGISTRATION SGFile: IBM Security Webinar - Best Practices & How Organizations Can Drive a Cybersecurity Behavioural Change Program - REGISTRATION SGlaunch -
 Document: IBM Security Webinar - Best Practices & How Organizations Can Drive a Cybersecurity Behavioural Change Program - ATTENDANCE SGFile: IBM Security Webinar - Best Practices & How Organizations Can Drive a Cybersecurity Behavioural Change Program - ATTENDANCE SGlaunch
Document: IBM Security Webinar - Best Practices & How Organizations Can Drive a Cybersecurity Behavioural Change Program - ATTENDANCE SGFile: IBM Security Webinar - Best Practices & How Organizations Can Drive a Cybersecurity Behavioural Change Program - ATTENDANCE SGlaunch -
 Document: IBM Security Webinar - Best Practices & How Organizations Can Drive a Cybersecurity Behavioural Change Program. - ATTENDANCEFile: IBM Security Webinar - Best Practices & How Organizations Can Drive a Cybersecurity Behavioural Change Program. - ATTENDANCElaunch
Document: IBM Security Webinar - Best Practices & How Organizations Can Drive a Cybersecurity Behavioural Change Program. - ATTENDANCEFile: IBM Security Webinar - Best Practices & How Organizations Can Drive a Cybersecurity Behavioural Change Program. - ATTENDANCElaunch -
 Document: IBM Security Webinar - Best Practices & How Organizations Can Drive a Cybersecurity Behavioural Change Program - REGISTRATIONFile: IBM Security Webinar - Best Practices & How Organizations Can Drive a Cybersecurity Behavioural Change Program - REGISTRATIONlaunch
Document: IBM Security Webinar - Best Practices & How Organizations Can Drive a Cybersecurity Behavioural Change Program - REGISTRATIONFile: IBM Security Webinar - Best Practices & How Organizations Can Drive a Cybersecurity Behavioural Change Program - REGISTRATIONlaunch -
 Document: Infoblox Advanced DNS ProtectionFile: Infoblox Advanced DNS Protection.pdflaunch
Document: Infoblox Advanced DNS ProtectionFile: Infoblox Advanced DNS Protection.pdflaunch -
Document: April 2020 Special Focus - Social EngineeringFile: April 2020 Special Focus - Social Engineering.pdflaunch
-
Document: Barracuda’s Complimentary Covid-19 Phishing Simulation and Awareness CampaignFile: Barracuda’s Complimentary Covid-19 Phishing Simulation and Awareness Campaign.pdflaunch
-
Document: Cybersecurity Asean Guide to Creating a Security Policy For Online Video MeetingsFile: Cybersecurity Asean Guide to Creating a Security Policy For Online Video Meetings.pdflaunch
-
 Document: Webinar-How To Monitor Your Growing Threat Landscape and Build a Consolidated PictureFile: Webinar-How To Monitor Your Growing Threat Landscape and Build a Consolidated Picturelaunch
Document: Webinar-How To Monitor Your Growing Threat Landscape and Build a Consolidated PictureFile: Webinar-How To Monitor Your Growing Threat Landscape and Build a Consolidated Picturelaunch -
Document: How The Falcon Platform Aligns With The CIS Critical ControlFile: How The Falcon Platform Aligns With The CIS Critical Control.pdflaunch
-
Document: C-Level Forum : Profiling Cybercriminals To Protect Your Data Privacy Event Summary E-bookFile: C-Level Forum : Profiling Cybercriminals To Protect Your Data Privacy Event Summary E-book.pdflaunch
-
Document: RMiT Compliance Executive Briefing Post-Event E-bookFile: RMiT Compliance Executive Briefing Post-Event E-book.pdflaunch
-
Document: CSA Decision Maker's Checklist for Choosing a Total Email Protection SolutionFile: CSA Decision Maker's Checklist for Choosing a Total Email Protection Solution.pdflaunch
-
Document: The Future of Cybersecurity in Asia Pacific and Japan – Culture, Efficiency, AwarenessFile: The Future of Cybersecurity in Asia Pacific and Japan – Culture, Efficiency, Awareness.pdflaunch
-
Document: Cyber Security CMAS Services by Ingram MicroFile: Cyber Security CMAS Services by Ingram Micro.pdflaunch
-
Document: Nefarious AI and AI-Based Cyber Attacks- Should We Be Afraid?File: Nefarious AI and AI-Based Cyber Attacks- Should We Be Afraid?.pdflaunch
-
Document: Do We Understand Malware in South Asia? Supported by MalwarebytesFile: Do We Understand Malware in South Asia? Supported by Malwarebytes.pdflaunch
-
Document: July Special Focus - The Cyber Threat Actor LandscapeFile: July Special Focus - The Cyber Threat Actor Landscape.pdflaunch
-
Document: What to Do BEFORE All Hell Breaks Loose: Cybersecurity for Today’s Extreme ThreatsFile: What to Do BEFORE All Hell Breaks Loose: Cybersecurity for Today’s Extreme Threats.pdflaunch
-
 Document: The Rise Of Machine Learning In CybersecurityFile: The Rise Of Machine Learning In Cybersecurity.pdflaunch
Document: The Rise Of Machine Learning In CybersecurityFile: The Rise Of Machine Learning In Cybersecurity.pdflaunch -
Document: Barracuda Email Threat Scanner for Office 365File: Barracuda Email Threat Scanner for Office 365 .pdflaunch
-
Document: State of Cybersecurity 2019File: State of Cybersecurity 2019.pdflaunch
-
Document: Cybersecurity Asean's Executive Guide Managing Email Cyber Risks supported by BarracudaFile: Cybersecurity Asean's Executive Guide Managing Email Cyber Risks supported by Barracuda.pdflaunch
-
Document: Malwarebytes Webinar: You Got Breached. Now What? Are You Secure in Your Security Strategy?File: Malwarebytes Webinar: You Got Breached. Now What? Are You Secure in Your Security Strategy?launch
-
Document: C-Level Cyber Security Round Table Supported by Ingram Micro, Fortinet & IBMFile: C-Level Cyber Security Round Table Supported by Ingram Micro, Fortinet & IBM.pdflaunch
-
Document: Top 7 Office 365 Security Use Cases for a CASBFile: Top 7 Office 365 Security Use Cases for a CASB.pdflaunch
-
Document: The Phishing Phenomenon: How To Keep Your Head Above WaterFile: The Phishing Phenomenon: How To Keep Your Head Above Water.pdflaunch
-
Document: 2019 CROWDSTRIKE GLOBAL THREAT REPORTFile: 2019 CROWDSTRIKE GLOBAL THREAT REPORT.pdflaunch
-
 Document: Webinar - Understanding the Tactics and Techniques of CybercriminalsFile: Webinar - Understanding the Tactics and Techniques of Cybercriminalslaunch
Document: Webinar - Understanding the Tactics and Techniques of CybercriminalsFile: Webinar - Understanding the Tactics and Techniques of Cybercriminalslaunch -
Document: Cybersecurity Asean Executive Briefing Note to Securing The Interconnected WorldFile: Cybersecurity Asean Executive Briefing Note to Securing The Interconnected World.pdflaunch
-
Document: July Special Focus - The Very Real IoT Cyber Threat supported by BarracudaFile: July Special Focus - The Very Real IoT Cyber Threat supported by Barracuda.pdflaunch
-
Document: Guide To AV ReplacementFile: Guide To AV Replacement .pdflaunch
-
Document: Where To Invest Next: Guidance For Maturing Cyber DefensesFile: Where To Invest Next: Guidance For Maturing Cyber Defenses.pdflaunch